
The Complete Gateway to Temporary Emails: Protecting Your Privacy in a Digital World.
The Complete Gateway to Temporary Emails: Protecting Your Privacy in a Digital World
In today's hyper-connected landscape, your primary email address has become a digital key to your identity. You use it for work, banking, social media, and subscriptions. But every time you enter it on a new website for a one-time download, a forum registration, or to access "exclusive" content, you expose that key to potential risks: spam, data breaches, and intrusive tracking.
This is where the strategic use of temporary emails transitions from a niche tool to an essential component of digital hygiene. Think of them not just as disposable addresses, but as your complete gateway to maintaining control and privacy online.
What Are Temporary Emails, Really?
A temporary email, also known as a disposable, fake, or 10-minute email, is a service that provides you with a fully functional email address without requiring any registration. This inbox is typically short-lived—lasting from 10 minutes to a few days—before it, and all its contents, are permanently deleted.
Their core function is simple: to receive verification or confirmation emails without linking them to your real identity.
The Triple-Layered Shield: Why This "Gateway" is Essential
1. The Impenetrable Spam Filter: This is the most immediate benefit. Use a temporary email for online shopping trials, app downloads, or webinar sign-ups. When the marketing emails inevitably start flooding in, they hit a dead-end inbox destined for self-destruction. Your primary inbox remains a clean, professional, or personal space.
2. Data Breach Containment: Major companies get hacked regularly. If a service where
you used a temporary email suffers a data breach, your real email address—often the linchpin to your other accounts—is not on the list. This containment strategy drastically reduces your vulnerability to credential stuffing attacks and phishing campaigns that follow breaches.
3. Privacy and Anonymity Preservation: Many websites monetize your data by tracking your activity and selling your email to advertisers. A temporary email severs this link. It allows you to access necessary information or services while keeping your digital footprint minimal and your personal profile anonymous.
Navigating the Gateway: How to Use Temporary Email Services Effectively
Using a temporary email service is remarkably straightforward, which is key to its power.
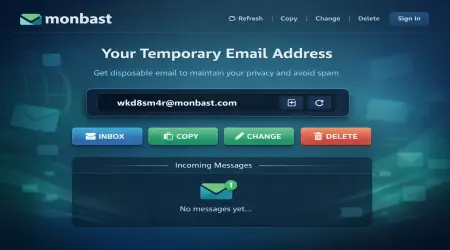
1. Visit a Provider: Go to a reputable temporary email service website (like TempMail, Guerrilla Mail, or 10MinuteMail).
2. Get Your Address: A random email address (e.g., `xjk45p9d@monbast.com`) is instantly generated for you. You can often refresh to get a new one or create a custom alias.
3. Use It: Copy this address and paste it into the website requiring email verification.
4. Receive Mail: Return to the temporary email tab. The verification email (or any other sent mail) will appear in the inbox automatically. Click the link or retrieve the code.
5. Let It Expire: Once done, simply close the tab. The address will expire according to the service's timeframe, leaving no trace.
Important Considerations and Best Practices
While invaluable, temporary emails are a specific tool, not a universal replacement.
Not for Permanent Accounts: Never use a temporary email for important, permanent accounts like banking, government services, your primary social media, or work-related platforms. You will lose access if you need to recover the account.
Limited Functionality: They are for receiving emails only, primarily for verification. Sending emails is usually not possible.
Choose Reputable Services: Opt for well-known providers that do not log your activity. Avoid obscure services that might compromise the very privacy you seek.
Conclusion: Your First Line of Digital Defense
Viewing temporary emails as your complete gateway to privacy reframes them from a simple tool into a strategic mindset. They are the digital equivalent of using a guest pass instead of your home key, a burner phone for a specific transaction, or a privacy screen on your laptop in a cafe.
In an era where personal data is the new currency, taking proactive steps to control its flow is not paranoid—it's prudent. By integrating the temporary email gateway into your online routine, you reclaim a measure of anonymity, build a powerful shield against spam, and significantly harden your defenses against the evolving threats of the digital world. Start using this gateway today; your primary inbox—and your privacy—will thank you.